How to create a self signed SSL certificate and how to use it with your web Server.
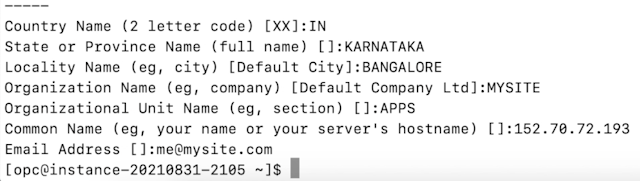
SSL certificate is the foremost important aspect of any website. If your website is running without SSL, modern browsers will stop the users from entering the website. Of course, there are ways to bypass that, at your own risk. As long as your website has no commercial data exchange, sensitive user information, etc, you are still good to run a website without a proper SSL certificate. For example, a blog can run without an SSL. Note that Google AdSense accepts websites without SSL. But the topic of this post is about Self Signed SSL certificate. How to create one, how to use it, and where to use it. Let us see where to use it. For any website which is used for internal purposes, it's always a good idea to use Self Signed SSL, instead of paying for a real SSL certificate. Internal I mean, within a company, team, or for personal uses, for testing purposes, etc. Now, let us see how to create a self-signed SSL certificate. What you need A Linux machine. O...